VulnHub | Odin Walkthrough
Odin ventured to the Well of Mimir, near Jötunheim, the land of the giants in the guise of a walker named Vegtam. Mímir, who guarded the well, to allow him to drink from it, asked him to sacrifice his left eye, this being a symbol of his will to obtain knowledge
Hello there, in this article we are going to go through the steps to get root in an easy Vulnhub machine called Odin. I’d advise you to first try it out yourselves! Come back if you are really stuck, or if you just want to see how I did it my way ;)

Enumeration
I assume you know how to set up boxes from vulnhub in your virtualization software of choice. If not here’s a quick guide for virtualbox. First off we need to find the ip of the machine. To do that, we need to scan our network, and so we need to know the ip range of our network. Run
ip a
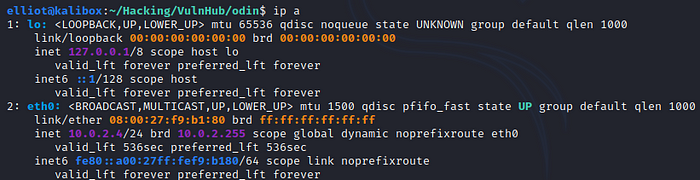
As we can see, my network is 10.0.2.255, with the prefix /24, so to scan our network to find the ip of the odin box we run
nmap 10.0.2.0/24
And we get this back

So its IPv4 address is 10.0.2.8 (Don’t forget though, from now on when you see 10.0.2.8, remember to replace it with the ip it has in your network). We see that it has port 80 open, but lets run a standard nmap scan to learn more
nmap -sC -sV 10.0.2.8

We can see that we are dealing with a wordpress site, specifically version 5.5.3. We can make a note of it for future investigation if we want. For now, let's go to the site. But before we do that, the box description asked us to add odin to our /etc/hosts file, probably for stability reasons. So open it with Vim( because what else would you use (:), and add
10.0.2.8 odin
Now all you have to do is write odin in your browser.
Initial Foothold

If you scroll down a bit, you will find this weird text
NB2HI4DTHIXS6Z3JORUHKYROMNXW2L3EMFXGSZLMNVUWK43TNRSXEL2TMVRUY2LTORZS6YTMN5RC63LBON2GK4RPKBQXG43XN5ZGI4ZPJRSWC23FMQWUIYLUMFRGC43FOMXXE33DNN4W65JOOR4HILTUMFZC4Z32EBZG6Y3LPFXXKIDONFRWKIDXN5ZGI3DJON2AU===
From the way it looks and the = at then end, you would think that it’s base64. But if you were to decode it, you would get back . This is because this is encoded in base32. So we need to change things a bit
echo NB2HI4DTHIXS6Z3JORUHKYROMNXW2L3EMFXGSZLMNVUWK43TNRSXEL2TMVRUY2LTORZS6YTMN5RC63LBON2GK4RPKBQXG43XN5ZGI4ZPJRSWC23FMQWUIYLUMFRGC43FOMXXE33DNN4W65JOOR4HILTUMFZC4Z32EBZG6Y3LPFXXKIDONFRWKIDXN5ZGI3DJON2AU=== | base32 -d
Which returns
https://github.com/danielmiessler/SecLists/blob/master/Passwords/Leaked-Databases/rockyou.txt.tar.gz rockyou nice wordlist
A link to the famous rockyou wordlist. What yhis means is that we’ll need to bruteforce our way to the wordpress admin panel, which can be found at wp-admin. There exists a tool specifically for wordpress bruteforcing called wpscan, here’s the link I used to refresh my knowledge on it. We need to run the appropriate command. But before we run it, we need a username.
One of the usernames I thought of was odin, so I wrote odin:odin in the login form

Unknown username is a peculiar choice of words. Lets try admin, another common username.

That’s what I like ;). Now that we know that admin is the username, we can go ahead and use wpscan
wpscan — url http://odin — passwords /usr/share/wordlists/rockyou.txt — usernames admin
After some other scans are executed and the guessing starts, wpscan quickly finds a match!

qwerty is the password. So now we can enter the admin panel.
Reverse Shell
Once in, we need to figure out how we can get a reverse shell. To do that I found this website, and followed the first way. I used the standard php script (Don’t forget to change the ip with that of your system and the port with that of your choice) and uploaded it to themes. After it got in, I set up a listener at the scripts default port
nc -lvnp 1234
And fired the curl command given by the website, after changing the host of course.

Bruh. There’s something else we should have changed, that being the path, as the theme wasn’t uploaded to 2020/12, but 2021/02


So let’s change the path accordingly, and try again

What can I say except that's what I like ;)
As a side note, I tried to spawn an interactive shell but didn’t have that much luck. If you do then write down in the comments how you went about it.
Privilege Escalation
Here you could do as I did and go to /home, search in those directories and all that. After a while I decided to try and access www-datas (the user we are now) home. I couldn’t remember where it was, and sh wouldn’t accept cd ~, so I changed shells with bash and went to the users home directory
bash;cd ~
There we find the html dir, and inside it we find multiple interesting php files

Where we find a potentially spicy wp-config.php. After catting it (nice word), we hit the jackpot

$6$e9hWlnuTuxApq8h6$ClVqvF9MJa424dmU96Hcm6cvevBGP1OaHbWg//71DVUF1kt7ROW160rv9oaL7uKbDr2qIGsSxMmocdudQzjb01
The root user hash as you would find it in /etc/shadow. All that’s left is to crack it. To do so, we first need to analyze it. Through some googling I came across a tool called hashid. What’s really good about it is the -m flag, which gives you the hashcat mode of the hash.
hashid -m ‘$6$e9hWlnuTuxApq8h6$ClVqvF9MJa424dmU96Hcm6cvevBGP1OaHbWg//71DVUF1kt7ROW160rv9oaL7uKbDr2qIGsSxMmocdudQzjb01’
Which returns
[+] SHA-512 Crypt [Hashcat Mode: 1800]
For the finishing blow, let’s run hashcat and get the hash
hashcat -a 0 -m 1800 passwordfile /usr/share/wordlists/rockyou.txt
I had already ran it, so I added — show to the of the above command. You should get back the password, which is jasmine.
su
And just like that, if we ran
id
We’d see what we wanted. The rest is quite typical

Welp, that’s all folks, hope you enjoyed it! If you’d like to see more write ups and articles from me then be sure to follow me and clap this article. You can also follow me on Twitter, and of course Github where you can check out some of my projects. Take care!










![[VulnHub] Basic Pentesting 1 Walkthrough](https://miro.medium.com/v2/resize:fit:679/1*JANl7kIdy5hCulMzoW7LpQ.jpeg)
