Vulnhub: Raven 1 Writeup (OSCP PREP) [by dollarboysushil]

Link to Raven 1: https://www.vulnhub.com/entry/raven-1,256/
Raven is a Beginner/Intermediate boot2root machine. There are four flags to find and two intended ways of getting root. Built with VMware and tested on Virtual Box. Set up to use NAT networking.
Note: I will be focusing on getting the root of the machine, I will not be focusing on getting the flag.
Disclaimer: Personally I didn’t like this machine
Nmap Scan

port 22 shh
port 80 http
port 111 rpcbind


Nikto scan result.

Running gobuster gives /wordpress hidden directory.

Since we have wordpress running , lets use wpscan

didn’t gave much info.

Then I tried enumerating the users by adding — enumerate u option
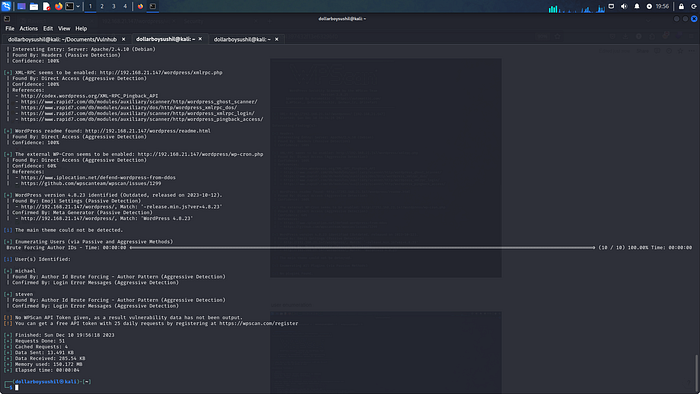
Which reveals two users michael and steven

Then I saved this usernames into username.txt

After running hydra to bruteforce , password is revealed.
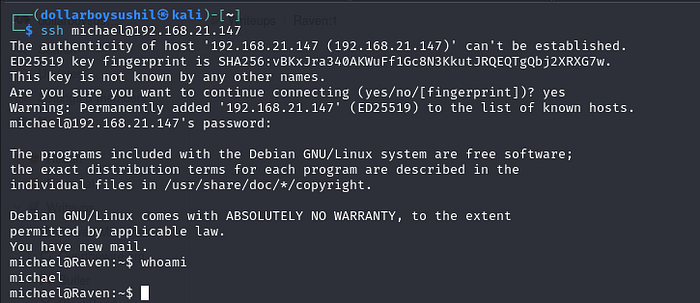
and we have shell as user michael


while digging around , i came across flag 2.

visiting /var/www/html/wordpress we can see wp-config which can have juice info.

And jackpot, we have mysql database credentials


and we have username and hashed password.
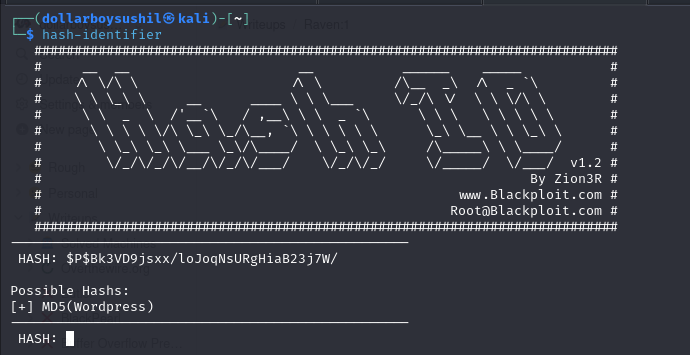
Then I used hash-identifier to identify hash type.

Running john gives us the password pink84
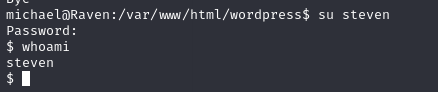
switch user to steven
Privilege Escalation

running sudo -l shows that user steven can run /usr/bin/python as raven

Looking at https://gtfobins.github.io/.
we can run command sudo python -c 'import os; os.system("/bin/sh")' to get root access.

and we got the root access.
For any correction / query /suggestion contact on
Instagram dollarboysushil
Twitter (X) dollarboysushil
Youtube dollarboysushil

