Vulnhub: TIKI 1 Walkthrough (OSCP PREP) [by dollarboysushil]

Link to vulnhub: https://www.vulnhub.com/entry/tiki-1,525/
Difficulty:
Easy
Goal:
Read flag from /
Victim IP: 192.168.1.136
Attacker IP (Kali Linux): 192.168.1.128

You can use netdiscover tool to find ip of tikisudo netdiscover
Reconnaissance

nmap -sC -sV 192.168.1.136-sC for default scripts,-sV for version enumeration and -p- to scan all ports.
Looking at the nmap result, we can see services ssh , http and smb running.

Visiting the IP we can see, Apache default page.

Viewing the /robots.txt we can see one disallowed entry /tiki

under /tiki we have tiki cms.

On clicking on login option, I tried to enter credentials like admin:admin admin:password and so on. None of which worked.
Lets Focus On smb service.

Using smbmap took we can list the available shares.
From the result, we have read access to Notes share.

Then we can login to Notes share.
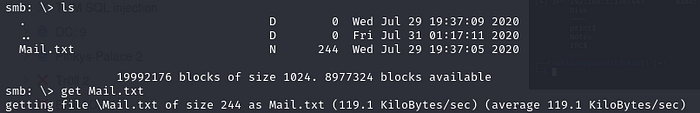
using ls to list files, we can see Mail.txt
Then use get command to download this txt file in your machine.

Reading the txt file we get CMS password 51lky571k1 for user silky

We can successfully logged in as user silky

Under Wiki section we can see List Pages option, under which we can see Silkys Homepage

Opening the Silkys Homepage we can see it is talking about CVE number .
Lets click on History option.

Using compare option we can see the CVE number CVE-2020–15906.
Using simple google search, we get more detail about this CVE.

From https://www.exploit-db.com/exploits/48927 , we can download the python exploit. Download it.

Then running the exploit we can see the usage command example.

Then running the exploit, tells use admin password is removed and telling us to use Burpsuite to login with admin without a password.
Fire up the burpsuite.
In CMS, enter username admin and any random password then intercept the request.

In the intercepted request, remove the password and forward request.

Doing so, should login as user admin
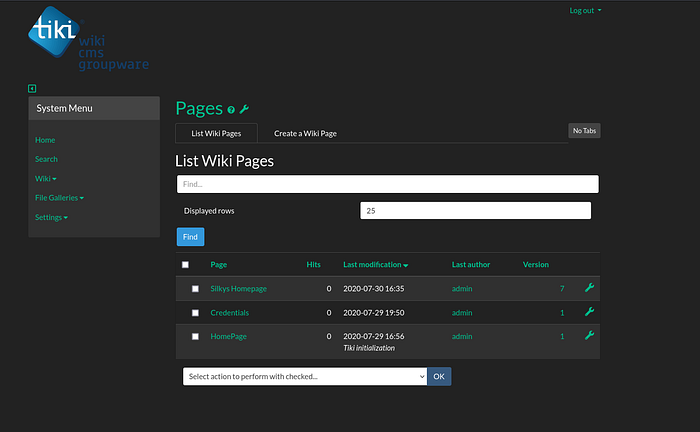
Under pages section, we can see a page named Credentials

Opening the credentials page, we can see credentialssilky:Agy8Y7SPJNXQzqA
Previously from nmap scan we know there is ssh service running, lets try to ssh login with this credentials.

It works.

using command sudo -l we can see user silky can run everything as user root.

then open bash using sudo command, we should have shell as user root.

Then we can visit root directory to view the flag.txt
flag:88d8120f434c3b4221937a8cd0668588
Thus completes this lab.
For any correction / query /suggestion contact on
Instagram dollarboysushil
Twitter (X) dollarboysushil
Youtube dollarboysushil









