Why Knowing How to Query is an Essential Cybersecurity Skill
At its core — cybersecurity revolves around data.
It’s logs, it’s analytics, it’s patterns waiting to be uncovered.
The true power in cybersecurity lies in the ability to harness this data in order to not only do your job, but to do it well.
And the key to unlocking that power? Knowing how to query data and shape it to your needs.
Yet, querying is often overlooked in favor of flashier skills like penetration testing, detection engineering, or automation.
But make no mistake, the ability to retrieve, organize, and most importantly — make sense of data can be a distinguishing factor in those who excel from those who merely just keep up.
Here’s what you need to know, and why you need to know it.
If you enjoy this article and want to be the first to see more like it, consider subscribing to my newsletter, the Cybersec Cafe, for free. I post content there first, and here second. Plus, you’ll get it straight to your inbox.
My goal is to deliver you value in various cybersecurity topics each week and to become your ultimate destination for expanding your expertise or for any aspiring cybersecurity professionals to break into the field.
Common Use Cases
Making Data-Driven Decisions
We live in the day and age of big data.
It’s taken the guesswork out of everything — just go where the numbers point you.
In cybersecurity, big data plays a massive role in driving direction throughout operations:
- SIEM: This is an expensive but powerful system. It’s important to be able to effectively leverage the massive amounts of logs being fed into this platform to drive the detection lifecycle. I wrote an entire article on how to do this here.
- User Behavior Analytics: Being able to search and understand user activity to recognize potentially malicious patterns could be the difference between a normal day and your company ending up on the news because of a massive data leak.
- Vulnerability Assessment: Scan results need to be parsed and prioritized quarter-over-quarter in the seemingly never-ending process that is vulnerability management. Finding an effective way to track scan results and progress is vitally important to keeping your organization critical vuln free.
- Security Posture Evaluation: The ability to correlate different services to understand the overall health of an organization and to identify areas for improvement is essential — especially in this industry, where distractions and small fires seem to pop up daily.
While you may not always “see” the data, it’s a driving factor of many different facets in every security team.
To make matters more complex, data lives in many different systems throughout your environment based on what is native and what makes most sense. Those who take the time to learn their own infrastructure and find ways to correlate data between systems can become infinitely valuable to their organization.
So, take the time to learn what logs live where, and prioritize learning the query language for the platform that is the best fit for your use cases.
Detection Engineering
The SIEM is the backbone of Security Operations, and detections are the engine that fuels it.
Every SIEM I’ve ever used leverages Query languages in ther detection engine — Splunk, Sentinel, Falcon, the list goes on (please correct me in the comments if there’s a SIEM that doesn’t have a query language for their detections).
Even Panther, which favors detections as Python, also has the option to use SQL for their detections through YAML or scheduled queries.
In order to create detections, you’ll also need to be able to search through your logs in order to understand how to write them.
Writing quality detections is a skill — and a valuable one at that. These rules function as real-time alerts throughout your environment and can often be the credited with finding threats before they can cause any harm.
A high-fidelity detection requires a deep understanding of the log source and the threat — a process that starts with a simple query.
Triage
The ability to triage alerts is almost an expectation nowadays for cybersecurity positions.
It’s a fundamental skill you’re just expected to have. Even if you’re in a position that doesn’t triage in your day-to-day, it demonstrates a basic understanding of security threats and the ability to think critically about data.
Active Triage generally comes in two flavors: Saved Queries and Ad-Hoc Queries (there’s also OSINT, but let’s stick to the logs here).
In order to leverage Saved Queries (templated queries created for specific use cases), you’ll need a basic ability to understand the query language so you can make adjustments for your specific investigation.
Then there are Ad-Hoc Queries, which are written from scratch during triage. This will require an understanding of the table schema, or the ability to figure it out. Saved queries won’t always get it done, but the best professionals can get their hands dirty without having to stress.
There’s also Automated Investigations, which are generally either performed in a SOAR, Jupyter Notebooks, or another workflow orchestration equivalent.
While these implementations are more technical use cases, the meat and bones of the automation is still built on queries.
Incident Response
This is the “hard mode” use case, and will really test your skills.
When stress and tensions are high, you’ll need to be able to trust your skills to query your systems quickly.
Most incidents that occur are new — meaning there are no Saved Queries or Jupyter Notebooks built out ahead of time to help automate your searches. You’ll have to be ready to roll up your sleeves in these scenarios.
It’s also not uncommon to find out mid-incident that there’s a new source of logs living in a platform you’ve never used before.
You may need to learn a new schema on the fly. Or better yet, a new query language.
While it will most certainly take time to get to this point, if you’re comfortable with one query language, it’ll be much easier to learn a different one quickly — especially if you know how to securely leverage AI as a sidekick.
But, if you’re already struggling with one, you won’t be as much of an asset for your team in these high stress situations.
The Basics
Now that you know why you need to learn a query language, let’s dive into the fundamentals you need to learn in order to be functional.
For starters, I’d recommend learning straight up SQL. It was developed in the early 1970’s, became commercially available in 1979, and is not going anywhere anytime soon.
Plus, many of the skills are transferable — many query languages are derived off SQL, and you’ll find many of the same principles in others.
SELECT
Select is how you control the data you see. Specify the columns you want, or use a wildcard (*) to select everything.
FROM
This is how you select your data source. Databases have many different tables which each have their own schemas.
WHERE
Here, you’ll write logic to decide what you want to retrieve. Some basic operations are:
- Equals: Notates as =, this retrieves whatever is an exact match
- Like: Notated as `LIKE ‘%test%’`, this function searches for a match where the % functions as a wildcard wherever it is placed
- Booleans: Basic boolean logic is necessary to understand to write quality queries, and essentially boils down to True/False statements

LIMIT
Specify exactly how many results to return.
ORDER BY
Order by a specific column value using the asc or desc operators.
GROUP BY
Great for compiling statistics from a table when used in conjunction with count(*) in the SELECT statement.
Sample Queries
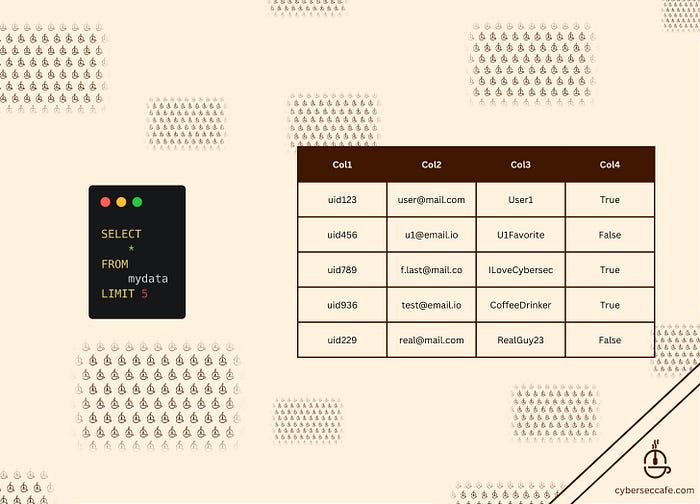
Query 1: Querying a new table? Use this basic query to query a few rows to get familiar with the schema and what the database looks like:
SELECT *
FROM mydata
LIMIT 5
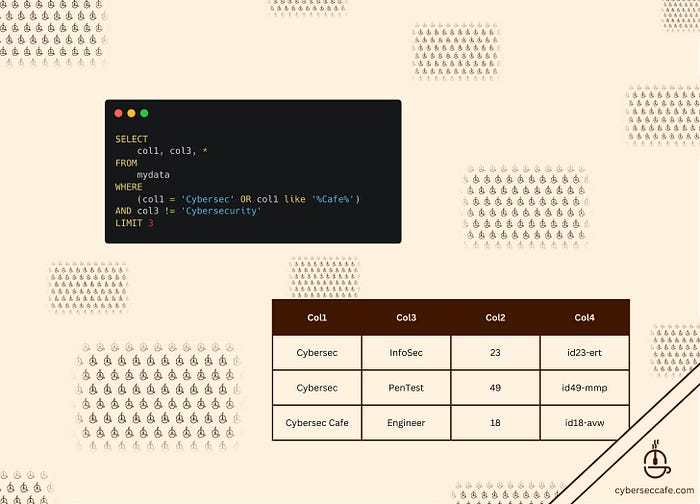
Query 2: This query returns 10 results of col1, col3, and every other column in the mydata table where col1 equals “Cybersec” or it has “Cafe” in it, and where col3 is equal to “Cybersecurity.”
SELECT col1, col3, *
FROM mydata
WHERE (col1 = ‘Cybersec’ OR col1 like ‘%Cafe%’) AND col3 != ‘Cybersecurity’
LIMIT 3
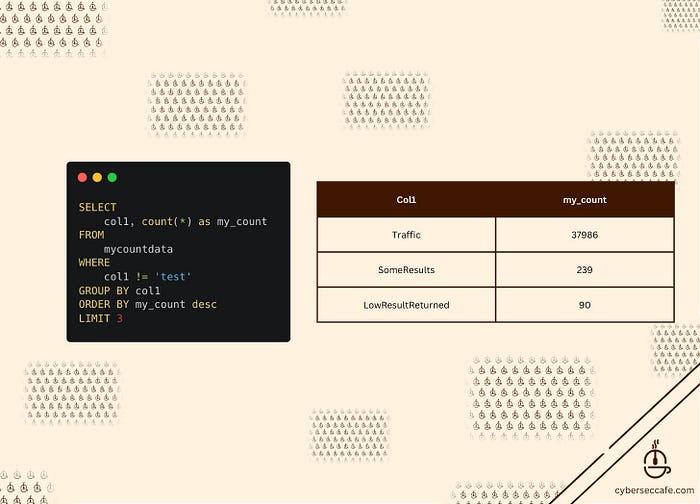
Query 3: This query returns the top 5 results, starting with the largest amount at the top, and searches for counts in the table for any value of col1 as long as it does not equal “test”.
SELECT col1, count(*) as my_count
FROM mycountdata
WHERE col1 != ‘test’
GROUP BY col1
ORDER BY my_count desc
LIMIT 3
-
It’s never too early, nor too late to start practicing your query skills.
It’s another one of those skills that you won’t be able to learn overnight, but consistent practice will yield significant results over time.
If you want to practice your Query skills, there’s a fantastic free resource online called SQLZoo.
It will teach you the basics, and work up to more complex operations as you work your way through the curriculum.
Start building the skills now that will make you an asset to any cybersecurity team.
—
Remember: The Cybersec Café gets articles first. Subscribe for free here.
Interested in getting into Cybersecurity? I have a course called the Security Sip. The curriculum is designed to help you build skills progressively over 12 sections, 85 modules, and 155 exercises. With rapidly evolving threats and technologies widening the skill gap, it’s time to secure your future in cybersecurity. Available Now!
Oh, and if you want even more content and updates, hop over to Ryan G. Cox on Twitter/X. Can’t wait to keep sharing and learning together!

