You're reading for free via Vivek PS's Friend Link. Become a member to access the best of Medium.
Member-only story
My Bug Bounty Journey: A Middle-Class Kid’s Quest for Free and Beyond
My article is open to everyone; non-member readers can click this link to read the full text.
“This story was originally published on my previous Medium account, which was unfortunately deleted. The original post garnered significant attention, with many views and followers, and I’m republishing it here to share my journey with a new audience and reconnect with readers who may remember it.”
Hello everyone,
I’m Vivek, a software developer currently working in a private company. This is the story of how I stumbled into the world of bug bounties — a journey fueled by curiosity, persistence, and my obsession with getting things for free.

Introduction
I first encountered the term “hacking” as a school student. Growing up in a middle-class family, I often dreamt of getting things for free. Whenever I came across something expensive that I couldn’t afford, I imagined building it myself using whatever I had at hand. I still remember trying to construct a computer using pens, paper, and cardboard sheets!
Computers didn’t interest me much until I opted for the Computer Science stream in higher secondary. Ironically, I hated the subject “IT” so much during secondary school that I even tried cheating on exams.
In 2006, my elder brother managed to buy a secondhand mobile phone from a friend. It was the era of GPRS, and we desperately wanted an internet connection to download games. Unfortunately, our pocket money wasn’t enough for Airtel recharge coupons.
One day, while exploring the phone, I stumbled upon a file titled “Hacking Airtel for Free Internet Access”. The word “free” immediately caught my attention. The file detailed proxy settings that could cheat Airtel and grant free internet access. That was the first time I understood “hacking” as a concept. From then on, hacking meant finding ways to get free internet!
Between 2000 and 2007, my curiosity about computers and programming grew. I was active in tech forums, constantly learning and experimenting. By 2007, I had joined an engineering college in the Information Technology stream. During my free time, I delved into networking and even coded computer viruses — purely out of curiosity.
In 2011, I began my career as a junior software developer, working on Windows applications. During this time, I developed an interest in reversing applications to crack them. For instance, I once discovered a loophole in TeamViewer that allowed me to bypass its usage limits. These small victories boosted my confidence immensely.
Discovering Bug Bounties
I first heard about bug bounties in 2015, but it wasn’t until 2017 that I seriously started learning about web application vulnerabilities. While working as a senior web developer, I began studying write-ups and registered on HackerOne. Despite hours of effort, I couldn’t find a single bug in any application.
Instead of giving up, I made it a habit to inspect web requests and responses whenever I visited a website.
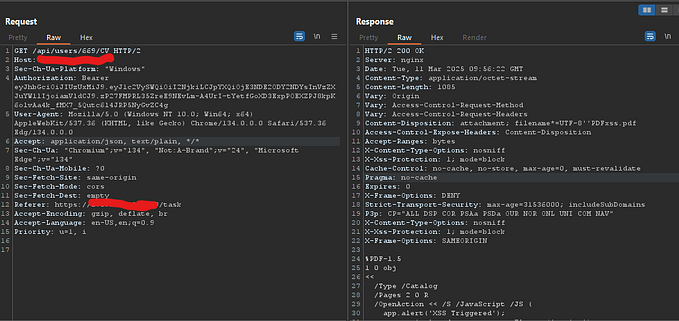
First Bug
After a lot of persistence, I finally reported my first bug in the e-commerce platform Myntra. It was a Cross-Site Request Forgery (CSRF) issue that allowed anyone to change the address of a user.
After reporting the bug, Myntra took weeks to respond. Frustrated, I repeatedly followed up but received no updates. Disheartened, I decided to stop pursuing it.
One day, while returning home from a chess tournament where I had performed poorly, I was sitting on the bus feeling defeated. Casually checking my email, I was overjoyed to see a response from Myntra: they had fixed the issue and listed my name in their Hall of Fame. That moment was unforgettable — I couldn’t contain my happiness.

Second Bug and First Bounty
Encouraged by Myntra’s recognition, I resumed hunting for bugs. My company was using Microsoft’s social network, Yammer, and I identified a vulnerability.
The platform allowed users to post images by pasting a URL in the comment section. Yammer fetched the image and created an objectId for it. I discovered that I could manipulate this objectId through a crafted web request, enabling an attacker within the network to change images posted by users.
Microsoft initially deemed the issue ineligible for a bounty because it involved a third-party service. However, they listed me in their Hall of Fame, which was a huge honor in itself.
To my surprise, three months later, Microsoft reevaluated the bug and rewarded me with $500 USD. I was ecstatic — I didn’t sleep that night!
The Journey Continues
That’s how my bug bounty journey began. It’s been a mix of learning, experimenting, and persistence. I’m still on this path, continually improving my skills.
I’ll share more write-ups about my experiences soon. Thank you for reading!